Data Encryption is still a best available mechanism when its about securing highly critical data stored in the cloud or on-premises. Organisational policies, or industry or government regulations, might require the use of encryption at rest to protect your data.
Server side encryption with AWS Key Management Service (KMS) is a highly available, scalable and secure service backed by Hardware Security Module (HSM). With KMS, the process of Key management has reduced to few simple clicks.
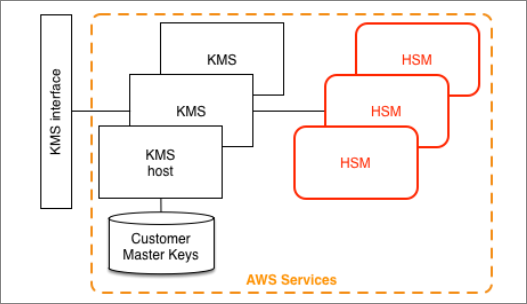
Quick Facts:
- KMS provides a centralised controlled access to your data using managed encryption.
- KMS is integrated with various AWS service like Amazon S3, EBS and Redshift.
- KMS usages audit logs can be accessed through AWS CloudTrail.
- AWS provides regional independence for customer data. Key usage is isolated within an AWS Region which means keys cannot be shared across different regions.
- AWS KMS provides cryptographic operations at latency and throughput levels suitable for use by other services in AWS.
Disadvantages of using KMS:
The drawback with custom KMS Keys is the complexity of setting up and managing the key policy. You will have to create and manage the policies and also will have to rotate the custom master key.
Type of Keys in AWS KMS
AWS Key Management Service supports two types of Keys:
- Customer Master Key
- Data Key
Customer Master Key:
Master key is also called as customer managed key or AWS managed key. A Master Key is used to encrypt data keys to securely store the encryption key. 4KB is the maximum size of the data encrypt or decrypt using KMS. Typically, you use CMKs to generate, encrypt, and decrypt the data keys that you use outside of AWS KMS to encrypt your data. This strategy is known as envelope encryption.
AWS Supports three types of CMK.
| CMK Type | Description | Can View | Can Manage |
| Customer Managed CMK | Customer managed CMKs are CMKs in your AWS account that you create, own, and manage. | Yes | Yes |
| AWS Managed CMK | AWS managed CMKs are that are created, managed, and used on your behalf by an AWS service that integrates with AWS KMS. | Yes | No |
| AWS Owned CMK | AWS owned CMKs are not in your AWS account. AWS owns and manages for use in multiple AWS accounts. AWS services can use AWS owned CMKs to protect your data. | No | No |
Key comparision between AWS managed CMK and Customer managed CMK:
| AWS Managed CMK | Customer Managed CMK | |
| Creation | AWS Creates on customer’s behalf | Customer generated |
| Rotation | Once every three years automatically | Once a year automatically |
| Deletion | Cannot be deleted | Can be deleted |
| Scope of Use | Limited to a specific AWS service | Controlled via KMS/IAM |
| Key Access Policy | AWS Managed | Customer Managed |
| User Access Management | IAM Policy | IAM Policy |
Data Key:
A Data Key is used to encrypt or decrypt the data inside a service or an application. Data keys are encryption keys that you can use to encrypt data, including large amounts of data and other data encryption keys.
Note: You can use AWS KMS Customer Master Keys (CMKs) to generate, encrypt, and decrypt data keys. However, AWS KMS does not store, manage, or track your data keys, or perform cryptographic operations with data keys. You must use and manage data keys outside of AWS KMS.
Steps to create a data key using CMK:
Step 1: call
- GenerateDataKey operation.
- GenerateDataKeyWithoutPlaintext operation, which returns only an encrypted data key.
Step 2: AWS KMS uses the CMK that you specify to generate a data key.
Step 3: The operation returns , as shown in the following image.
- a plaintext copy of the data key and
- a copy of the data key encrypted under the CMK

Decypt data using Data Key
To decrypt your data,
Step 1: pass the encrypted data key to the Decrypt operation.
Step 2: KMS uses your CMK to decrypt the data key and then it returns the plaintext data key.
Step 3: Use the plaintext data key to decrypt your data and then
Step 4: Remove the plaintext data key from memory as soon as possible.
